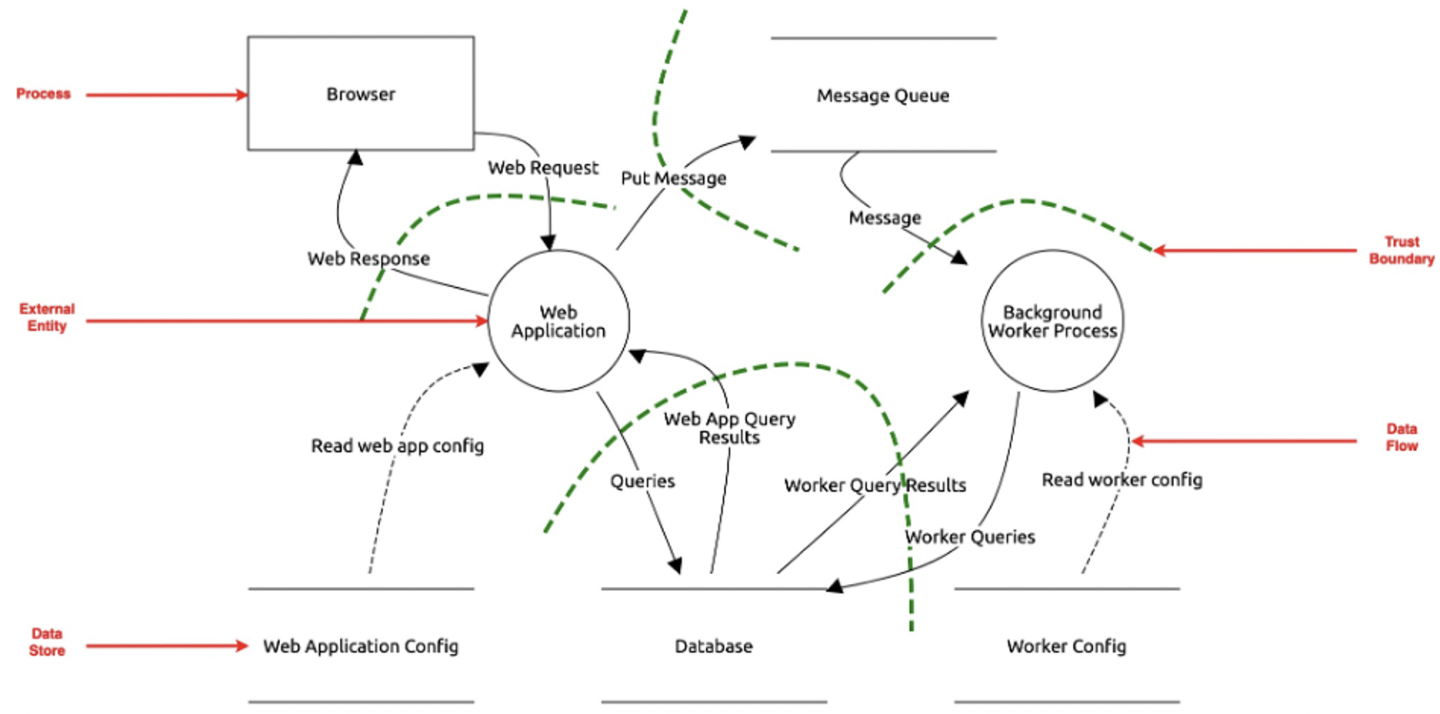
An Analysis of Open-source Automated Threat Modeling Tools and Their Extensibility from Security into Privacy | USENIX

Overview of systematic threat modeling in automotive secure development... | Download Scientific Diagram

Threat modelling connected and autonomous vehicle cybersecurity: an overview of available tools – Secure-CAV


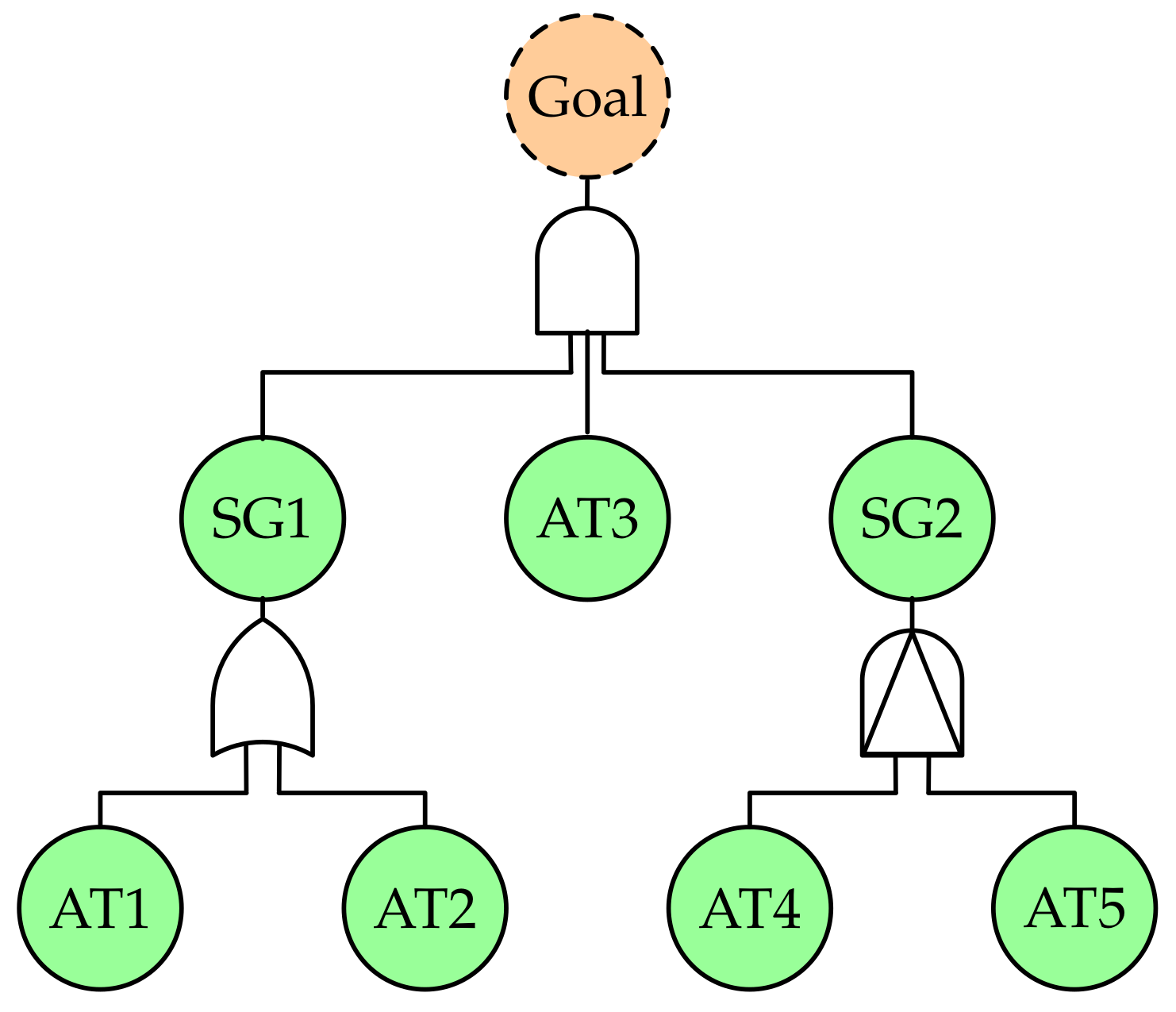



![PDF] Threat Modeling for Automotive Security Analysis | Semantic Scholar PDF] Threat Modeling for Automotive Security Analysis | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7f34f8b0a640926ab97e4fafe266dc8a4efdfa59/3-Figure1-1.png)
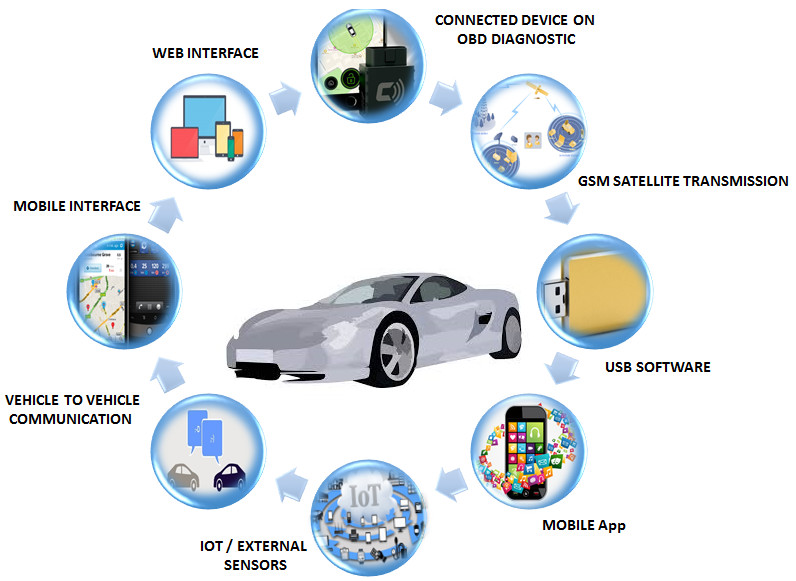
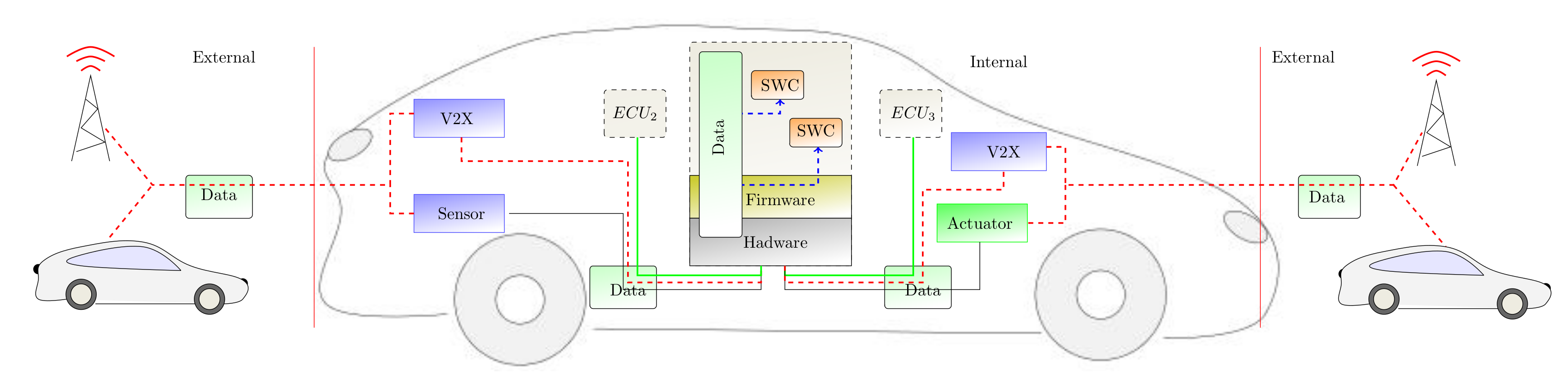


![PDF] Threat Modeling for Automotive Security Analysis | Semantic Scholar PDF] Threat Modeling for Automotive Security Analysis | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7f34f8b0a640926ab97e4fafe266dc8a4efdfa59/5-Figure2-1.png)
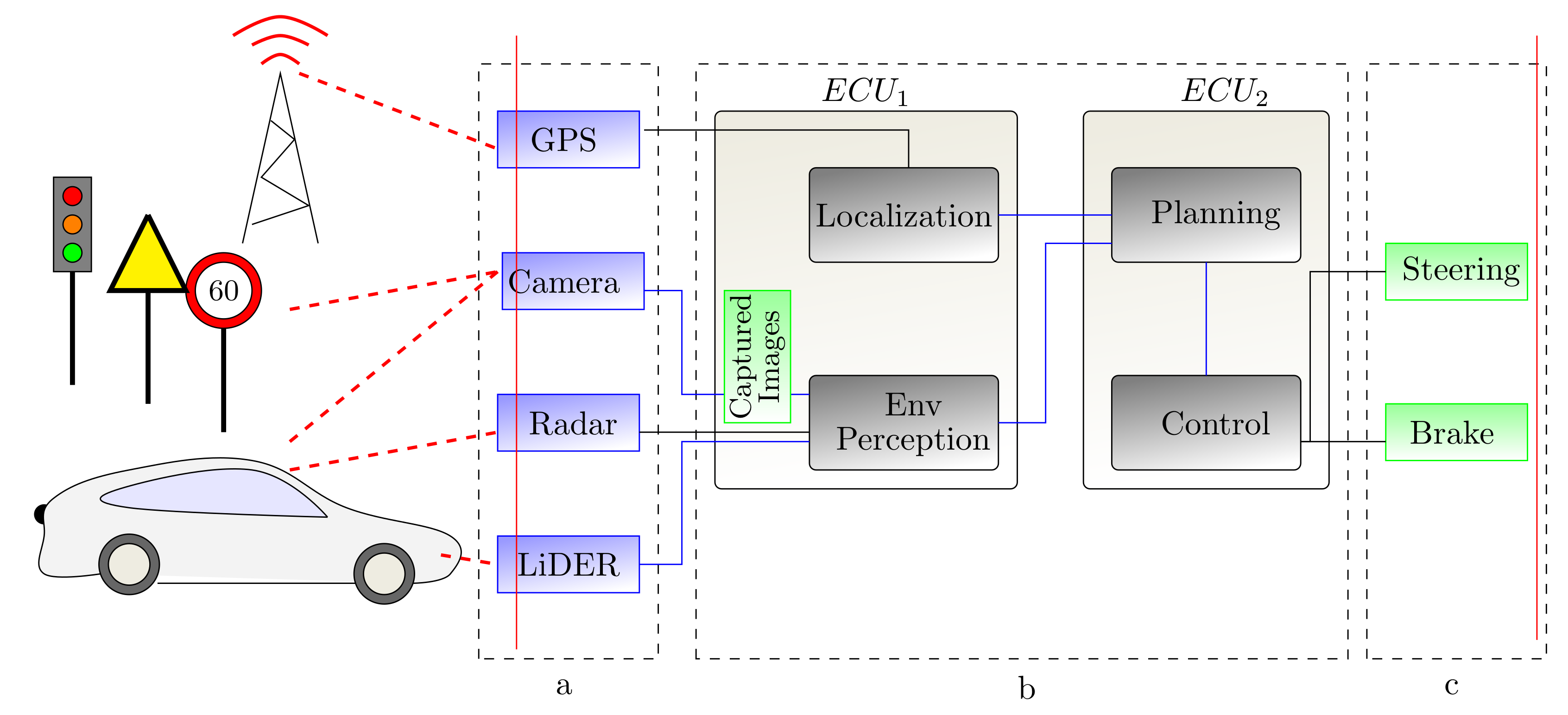
![PDF] Adapting Threat Modeling Methods for the Automotive Industry | Semantic Scholar PDF] Adapting Threat Modeling Methods for the Automotive Industry | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/16d814d2de41b3074b354976eeb19442ea350462/8-Figure5-1.png)



