Bit set, reset, toggle and masking in Microcontrollers | My journey with Microcontrollers and Electronics

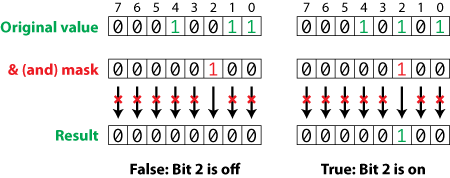
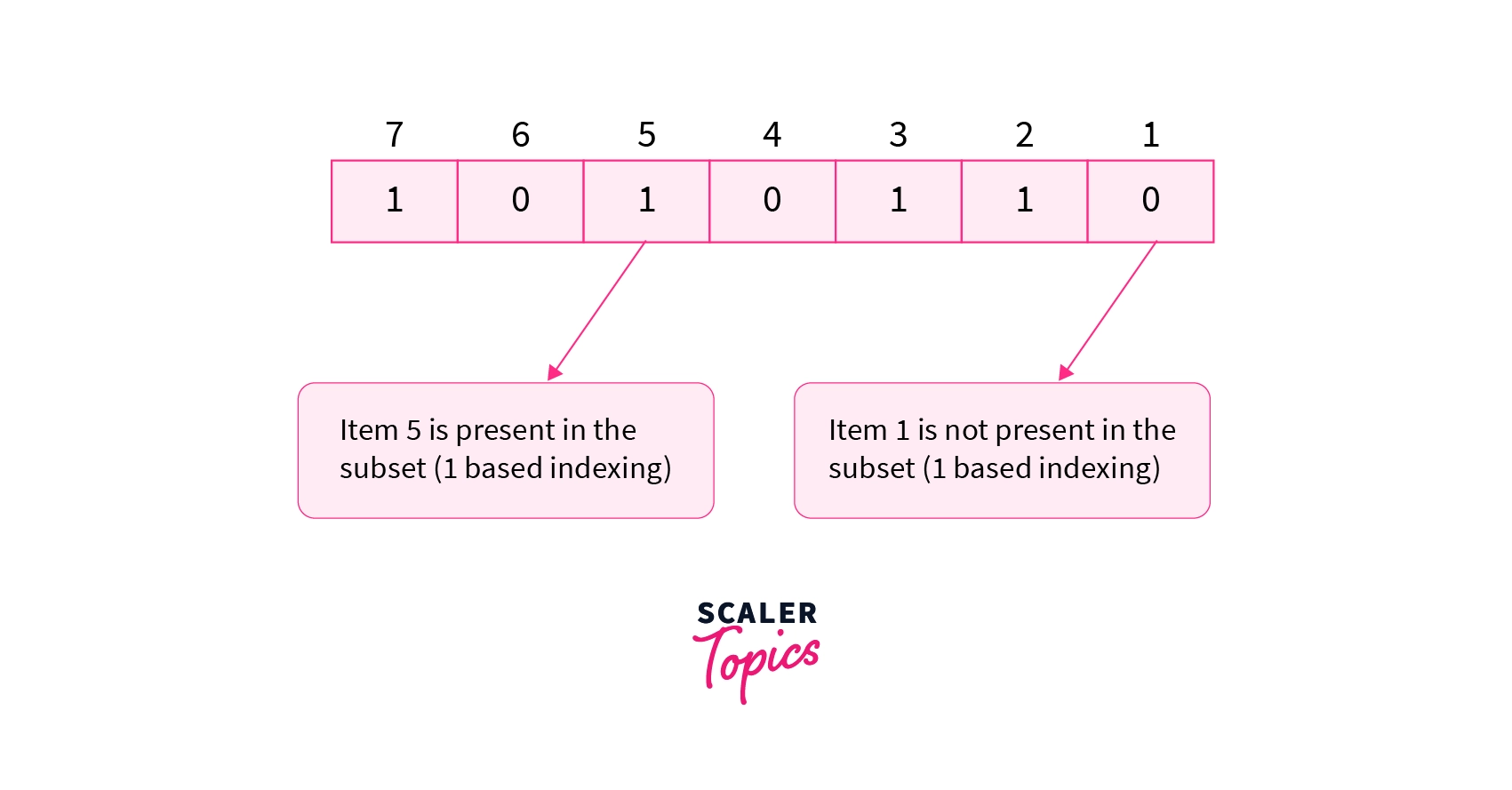
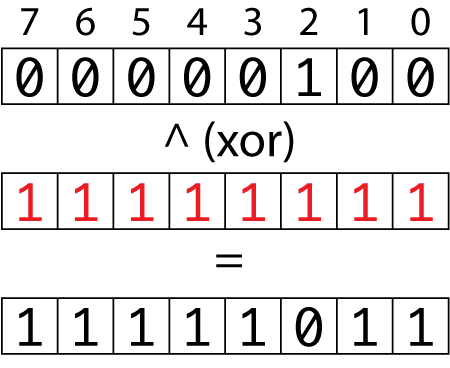
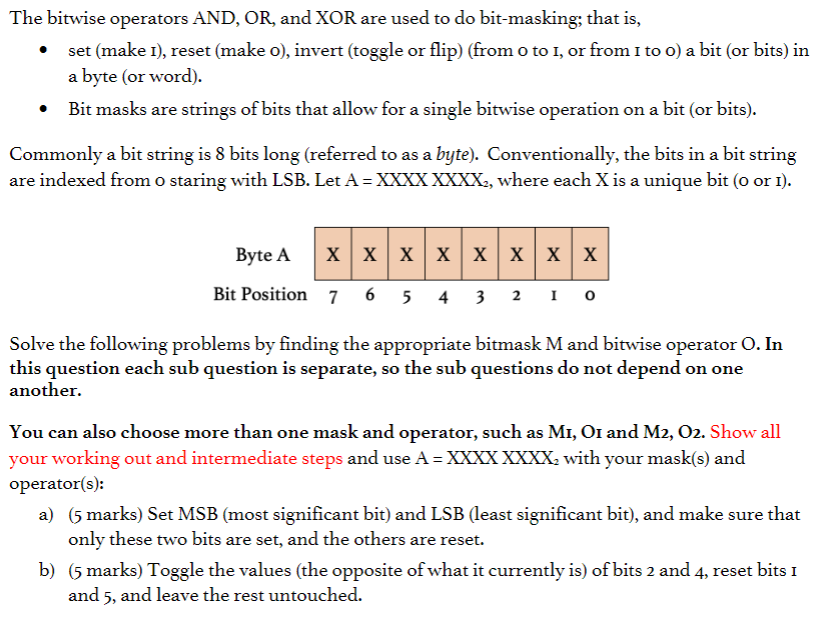
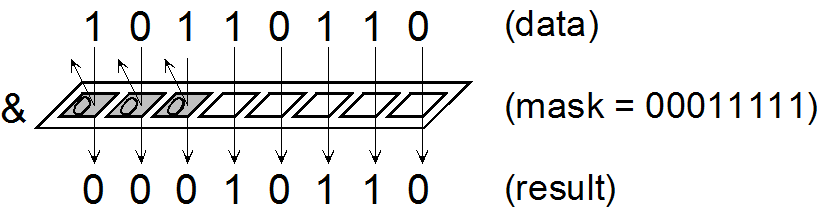
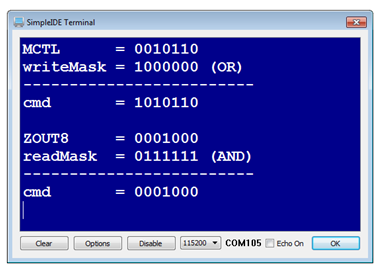
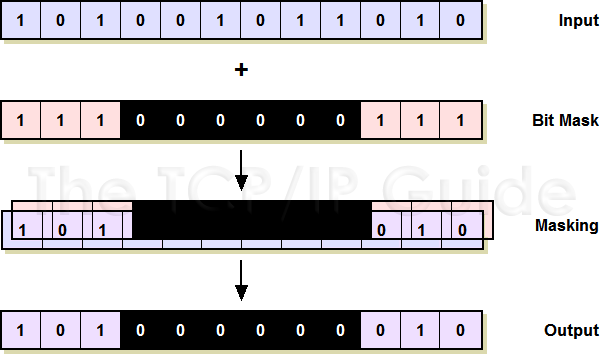
Bit Masking To access or affect only the bits we want, we need to construct a byte with bits set in the locations of interest – This byte is called a ' bit. -
![Illustration of word-masking and bit-masking schemes [49] for (a) a... | Download Scientific Diagram Illustration of word-masking and bit-masking schemes [49] for (a) a... | Download Scientific Diagram](https://www.researchgate.net/publication/337474031/figure/fig16/AS:828630175342605@1574572237341/Illustration-of-word-masking-and-bit-masking-schemes-49-for-a-a-positive-number-and.png)